Cybersecurity is one of the largest, fastest growing fields that the world has at this time. As I am writing this article the experts in the field indicate that we are missing more than 3.5 Million experienced cybersecurity professionals. Not mention that the breadth of cybersecurity overall. A quick Google Search on cybersecurity topics yields a result of more than 72 Million pages (TLDR;).
This article is dedicated to all of the businesses that have developed their own Cyber Security Teams from within. While I applaud the initiative, I also know that the road to understanding the different subjects for cybersecurity come from more than one training class, and more than 6 months in service to support the cybersecurity initiative.


Wait a minute
Let’s first review what the title of the article says. Your IT Staff doesn’t perform Cybersecurity functions. At first glimpse of this statement, you may or may not agree, but allow me a moment to explain further.
IT Staff members and Cybersecurity professionals have different skill sets. According to CareerBuilder.com this is their definition of ‘what is the function of an IT department’.
For the sake of this article, lets agree that this is a simple explanation of the requirements for a company’s IT department. Conversely, the cybersecurity department has a completely different set of functional requirements. The results of a google search for ‘what is the function of a cybersecurity department’ yields a smaller result set of over 33.3 Million pages (still too long to read in my lifetime). Here’s one of the higher level definitions.
Cyber security starts with everything outside of the computer
As you may be able to tell, the cybersecurity team is responsible for a completely different role in protection for the organization. You might say that they rely on the IT Department to create and maintain the functional environment.
This doesn’t cover any of the following topics either:
⦁ Developing a Cyber Risk Strategy
⦁ Including policies, procedures and strategies
⦁ Implementing compliance requirements and assessments
⦁ Testing the security controls in the environment
⦁ Assessing the security with software being developed
⦁ Including the security for third party software as well
⦁ Running Red Team security assessments against the Blue Team
⦁ The IT department is generally the Blue Team
⦁ Creating the regulatory compliance for the organization
⦁ Developing education for the company on what security is, and how what they do daily does matter.
There is much more that the security teams are responsible for within an organization, but the above are a sampling of the activities which the security teams are generally created to fulfill.

Experience Matters
Compliance isn’t an endpoint
Preventive vs. Reactive Security
IT Security Solutions recommends at least an annual Security assessment to determine the security posture and formal detection of internal activities.
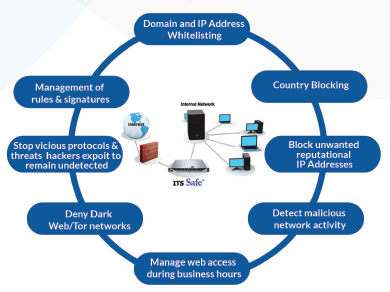
IT Security Solutions, Inc. is a Pittsburgh based technology company with 25+ years of cyber security domain expertise catering to businesses of all sizes. The solutions offered range from technology security audits and penetration testing to continuous network scanning. The company recently launched ITS Safe™, a proprietary managed security solution that blocks hackers from attacking networks - the largest IT security threat facing businesses today.
Contact IT Security Solutions to discuss how a paradigm shift will benefit your company today.

