“You are One Hack away from losing either your Job, or your business.”
Holly Ridgeway, CISO of PNC Bank 2012 to 2015
This article is about protecting your Business, and keeping it safe from the Intruders, before they are able to drain your business of your assets, clients and intellectual property. Much of what we do today depends on the Internet for Communicating, Selling and Marketing now, but the tools we depend on are ill prepared to protect, or even detect that a breach has already occurred.


The IT Team sees only the tip of the iceberg.
We rely on the computers and other equipment in our businesses on a daily basis to be able to send emails, print invoices, make sales, and so much more. The equipment needs to be maintained, updated and of course replaced.
We consider the people that keep our technology running to be geniuses because they do things that we do not understand. However, what they understand about the Computer equipment, stops at the equipment. The Firewalls and Virus scanners that are used barely touch the surface for protecting our networks, our businesses and our data. For everything that leaves the computers, the cyber security team needs to be in charge.
Cyber security starts with everything outside of the computer
The security of the environment needs to be developed and tested by a separate team, the cyber security team. The cyber security team validates the security which was included in the network, and whether or not the proper security controls are in place to protect the organization. It’s important to understand that asking your IT Team (internal or outsourced) to test the security of the organization is like permitting your teenagers to set their own curfew.
The reason for this is that they don’t understand what cyber security is, or what the Hackers are doing to infiltrate your environment.
The Security Assessment is a vital security activity that is recommended for all businesses. Yet, more than 77% of businesses don’t perform them annually, if at all. Then they wonder why they have had a breach, or worse yet, Ransomware.

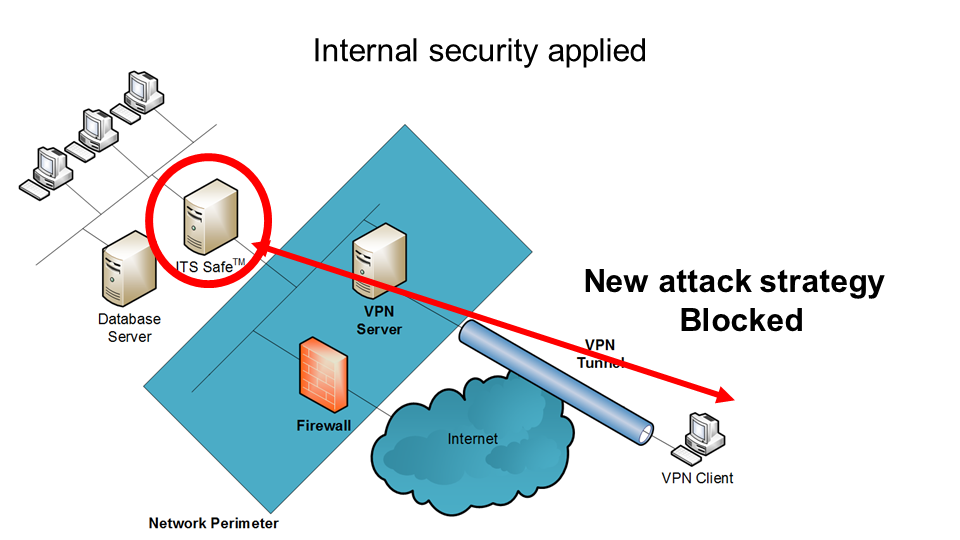
Why the tools that use today do not stop the malicious attacks.
One of the reasons why the tools you have, are also available to the intruders as well. They already know how best to beat these tools, and have found new ways to get inside our networks, our computers, and our phones. How safe can you really be if the Intruders are already inside your business?
Recently we have taken our ITS Safe™ Security Appliance to businesses to test their network and the existing security they have. In every case, we have discovered Intruders already inside the business’s secure network. In every case, the business was protected with a Firewall and Virus Scanners on every computer. Even when the business was protected with advanced firewall tools, the intruders were already inside the network.
While the IT departments had the best intentions to deploy their known security tools, none of the “Off the Shelf” solutions protected the organizations. None of the organization were aware that they were already compromised either. Today’s Intruders are different, they are able to wait quietly, and remain undetected inside the network until they have exactly what they were looking for.
ITS Safe™ Detects, Protects and Destroys Intruders.
This is why we created the ITS Safe™ Security appliance, to help businesses be safe. ITS Safe continuously reviews the network traffic and eliminates the threats before they are allowed to reach their destination.
One more thing about the need for the security assessment. More than 68% of recent security breaches were due to issues with poor security implementation, misconfigured firewalls, or assessments performed by the IT Dept which indicated these problems but were never corrected.
This is why it’s essential for your business to have an annual Security Assessment (like your medical checkup), and to have ITS Safe continuously monitor your network for the malicious activities which your security tools are not stopping.